what is an iot system
IoT or Internet of Things is a large set of interconnected devices capable of sharing data amongst them for monitoring and control. A edge system is a location with multiples of devices installed and connected to the main network. There can be – not necessarily be – a central control and monitoring system which provides interconnection, Human interface and management of the devices in the network.
[expand]
In an IoT system, one should be able take decisions in real time and allocate priorities to specified devices or actions. It cannot operate using conventional mode but using Real Time Operation System with definite and assured time of detection and activation.
When it comes to AIoT systems, the processing power of the data collation nodes or even the sensor or actuator nodes are enhanced to support AI algorithms. Thus, enabling ubiquitous computing and intelligence.
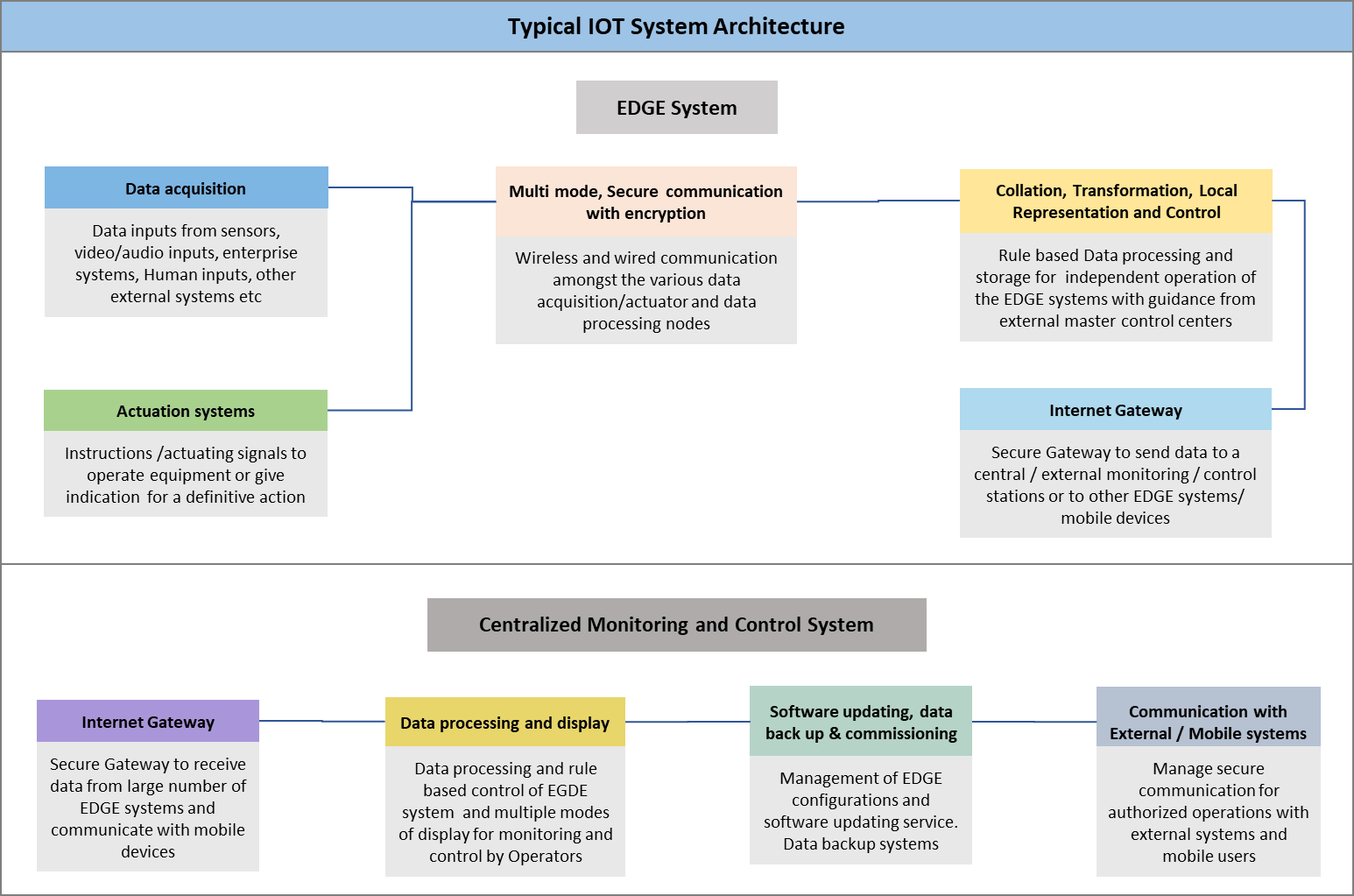
Webyfy IoT provides end to end hardware devices and software systems which supports conventional IoT, IIoT and AIoT systems. The REACH Framework has the ability to plot the required processes and create the specific solutions with very low cycle time of a few days even for the most complex of systems.
[/expand]
REACH – The IoT Solution Creation Framework
REACH is a bundle of technologies designed by Webyfy IoT to configure an IoT solution with ease by a business domain expert. It contains scores of hardware modules and hundreds of software modules..
[expand]
REACH is designed:
- to seamlessly integrate video, audio, sensor and actuator systems.
- to create multiple types of applications for multiple domains.
- to manage thousands of distributed systems.
- to enable rapid prototyping and in service alteration.
- to facilitate real time execution of complex rules.
- to facilitate rapid customization without any additional software/hardware development.
- to integrate industry standard hardware.
- to enable easy and effective integration of devices with low tech manpower.
- to make maintenance easy and increase reliability & availability.
- to assure the quality of individual module which will ensure the quality of the entire system.
- to enable continuous development of functional or technology modules with backward compatibility.
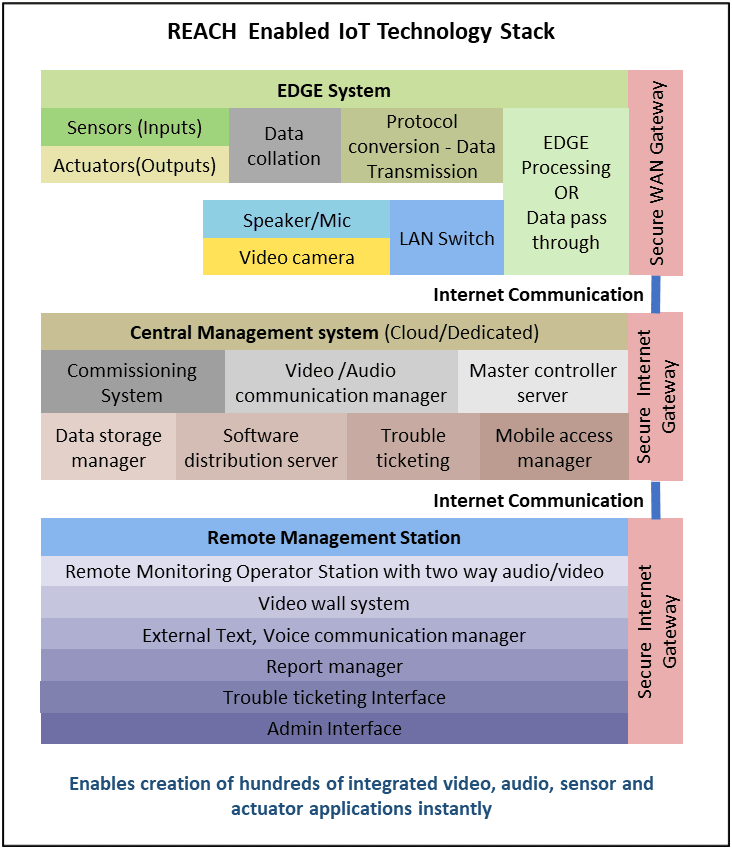
[/expand]
Video and Audio network
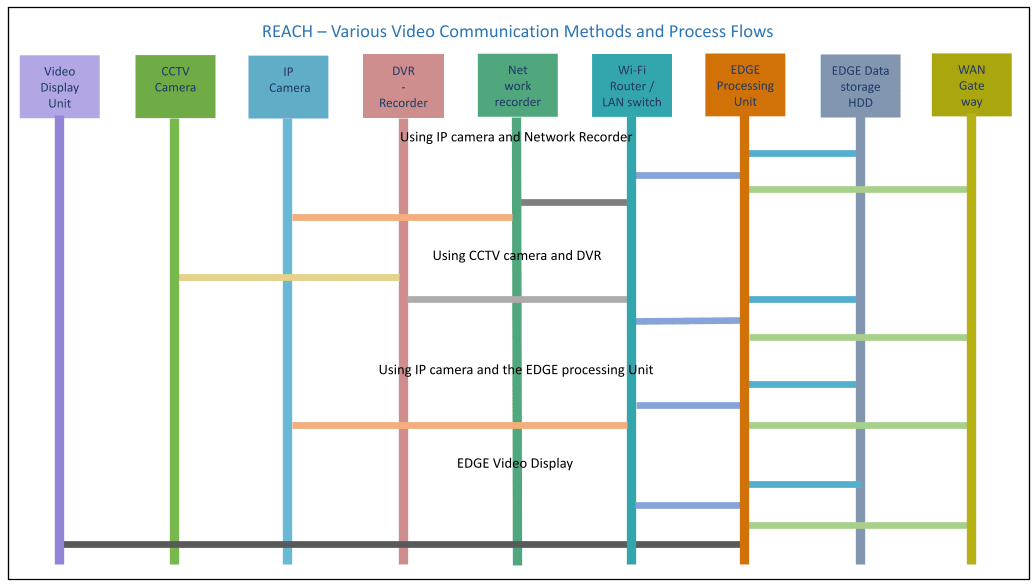
REACH has the capacity to support all types of cameras and operate the Pan, Tilt, and Zoom movements. It follows the ONVIF standards and other custom standards can be easily integrated. ONVIF (Open Network Video Interface Forum) is a global and open industry forum that promotes a global open standard for the interface of physical IP-based security products. Learn More
[expand]
The diagram shows different types of video functions are interconnected
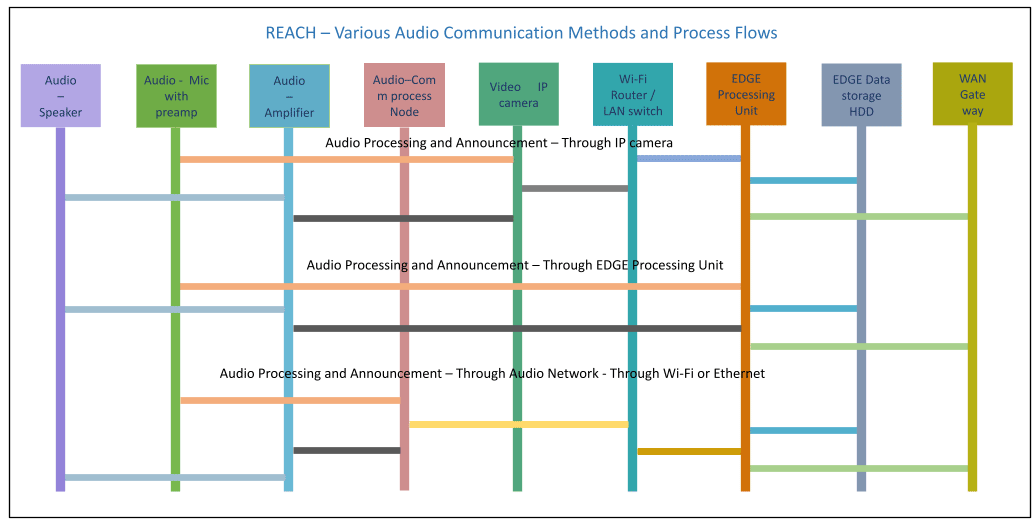
REACH supports multiple methods of interconnecting the audio devices. Webyfy has developed its own protocol for interconnecting audio devices – Microphones and audio amplifier/speakers. The audio communication processing node helps to interconnect using Wi-Fi, Ethernet, 4G modes of communication. As many numbers of microphones and announcement devices can be connected and individual device can be accessed.
[/expand]
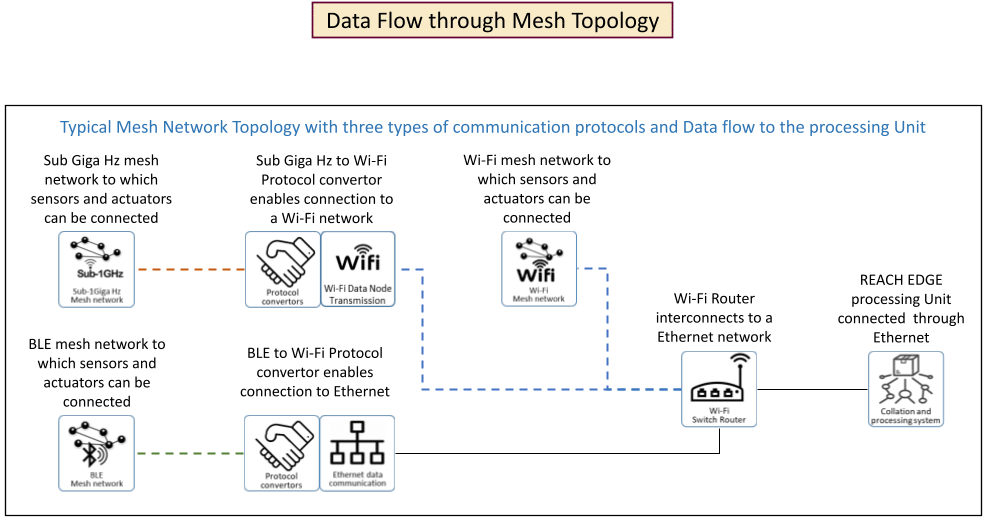
Data Communication
One of the main advantages of REACH is its capability to communicate in multiple data communication protocols. It has the capacity to interconnect any protocol to any other.
[expand]
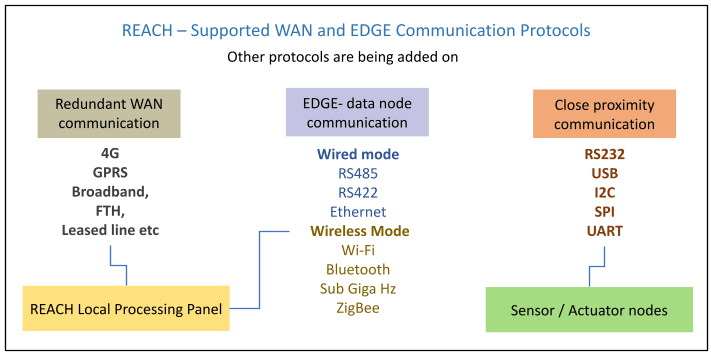
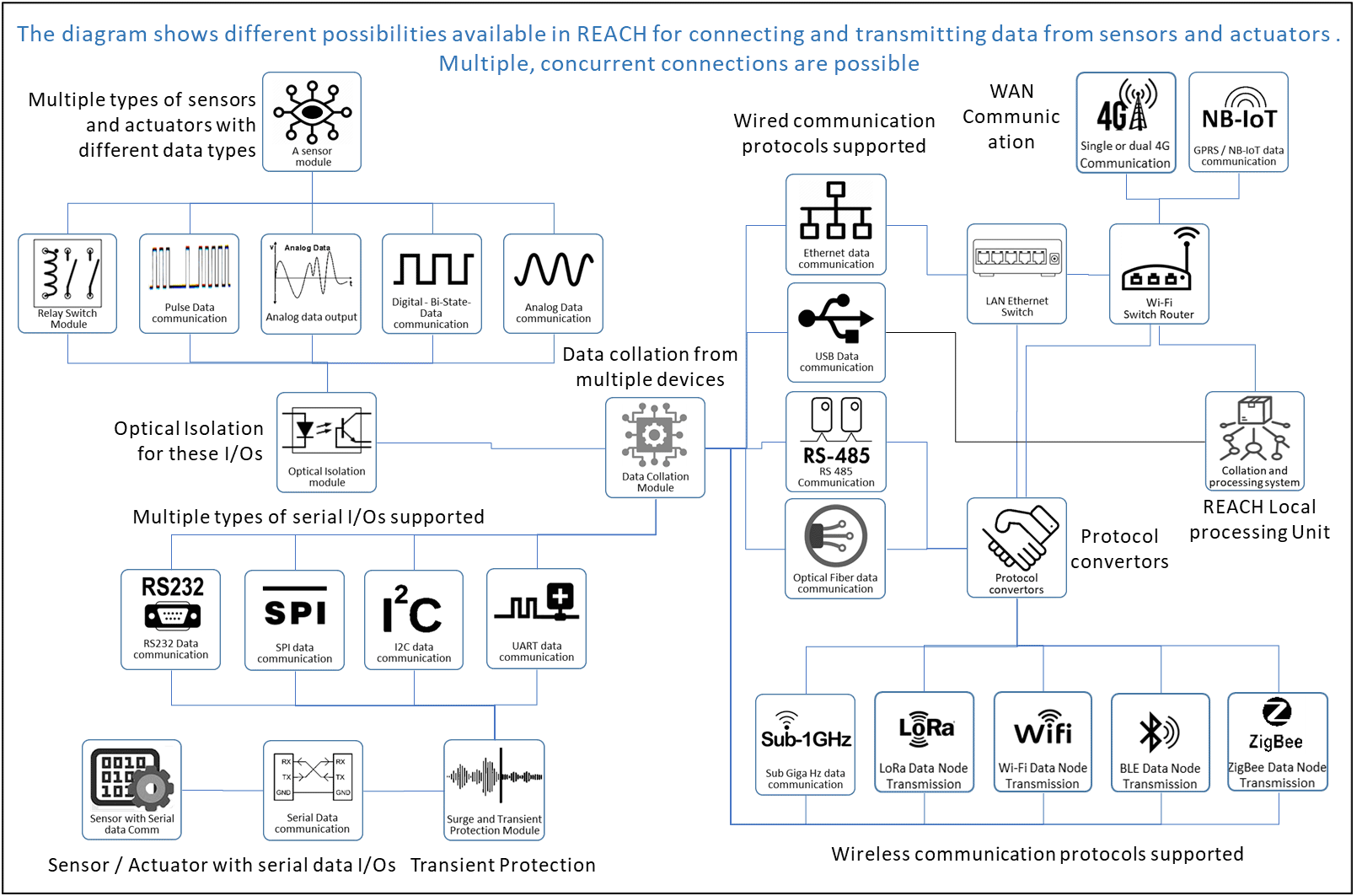
The following diagram is an indication of the protocols supported and their interconnection.
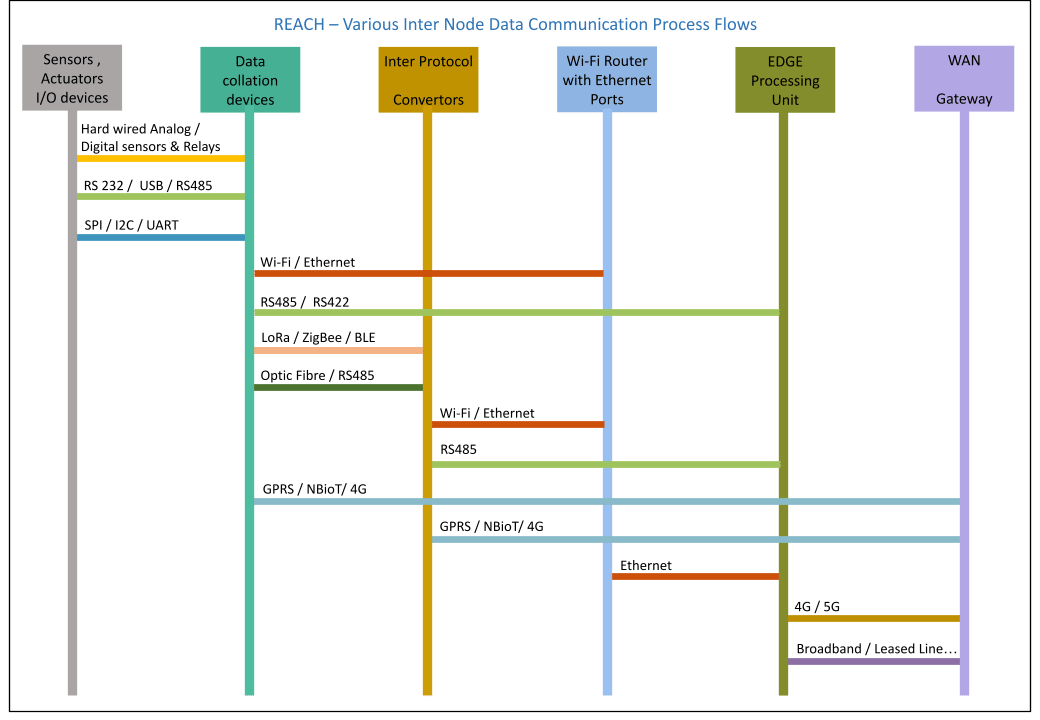
The diagram below shows the data flow for respective protocols in the REACH EDGE system
[/expand]
Sensor /Actuator Network
The sensors are of different types but can be broadly classified as ones with outputs like ON/OFF, Analog signals, PWM, or multiple types of serial data. REACH has the capability to integrate all types of sensors including custom sensors or actuators.
[expand]
Webyfy IoT has also designed and fabricated several sensors that are commonly used in applications. It is in the process of expanding the sensor actuator basket.
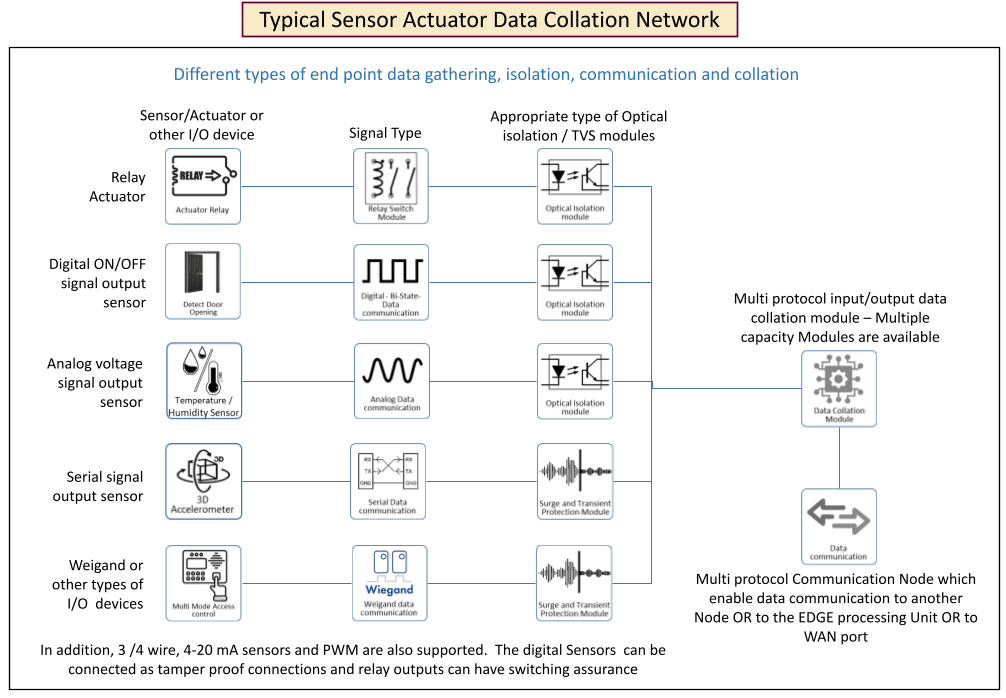
The sensors are connected to specific terminals according to the type which in turn communicates with Data Collation devices. Webyfy has designed the system to be very rugged and fail proof by incorporating 6 kV Optical isolation and also with adequate transient protection. Webyfy IoT has also designed tamper proof digital sensor connection as well as activation assurance and output current measurement relay modules. It can also provide Analog and PWM outputs in addition to relay activation.
The system also supports mesh network along with interconnection capability.
Generic sensors and their utility
| Flow meter for water outflow through large pipes | Pan, Tilt and Zoom camera to scan large area | Flow control system for water release system | |||
| Flow meter for water outflow through sluicegate | Indoor cameras | 3D accelerometer to detect movement, vibration, movement | |||
| Dam water level sensor | Outdoor cameras | Motor control/ integration with motor controller for remote management | |||
| Water level sensor module with data transmission facility | Microphones with data transmission capability for audio surveillance | Solar Modules for powering the remote sensor /actuator system | |||
| Earthquake sensor on the dam structure or other locations | Speakers to make announcements for audio surveillance | Multi authentication module for access control and attendance monitoring | |||
| Weather station module with data transmission facility | Hooters to warn of imminent danger or a critical situation | Panic Switch at appropriate locations to indicate an emergency situation | |||
| Independent water release warning stations for down stream locations | Water high / low level sensor for water pumping system | Harmful gases and environment sensor | |||
| Water seepage Detector | Shutter open /Close sensor | Detect availability of electrical power – 3 phase | |||
| Glass brake /vandalism sensor | Detect temperature at multiple points like inside a electrical control panel | Metering of electrical power consumption | |||
| People Presence using infrared sensor | Detect fuel levels in diesel fuel tank- typically that of a DG set | AC Voltage sensor | |||
| Vibration sensor for detecting banging, water turbulence, vandalism | Temperature and Humidity sensor – Interior and ambient | DC Voltage sensor for monitoring battery banks | |||
| Door Open / close position sensor for access detection | As an input for automatically operating lights | Earthing effectiveness sensor for ensuring electrical safety | |||
| Detect shifting of equipment from its position | Temperature sensors on the surface of transformers in a substation | Monitoring quality of power which affects operation and health of equipment | |||
| To give warning of a detected fire hazard | Fire / Smoke Sensor | Fire alarm to indicate the occurrence of fire at a location |
Webyfy has developed software modules which can use multiple sensor inputs and specific logics to detect a condition. Examples are given below
| Determine and ascertain the presence of people in a given location | Detect loss of air-conditioning and duration of malfunctioning | Determine the duration of presence of people in a given location | |||
| Detect loss of lighting or detect the non working of a set of /a light fitting | Detect presence of objects that did not belong to a location | Early detection of the chance of fire at a location | |||
| Detect vandalism attempt at a location | Monitor the actual status of functioning battery like charging , discharging or floating conditions and the deviations | Detect distress and scream at a location | |||
| Power supply monitoring including the quality of power supply | Detect masking of video camera lens and loss of video signals | Check if the machines are operated as per schedule and the deviations | |||
| Detect welding and gas cutting at a location | Check if the operational status of machines and its operating parameters and their deviations |
[/expand]
Integrated Network and Centralised Management
REACH is capable of integrating a large number of devices in one site or in hundreds of sites across geographies into a single entity.
[expand]
There is no limit to the number of Devices, Locations, Sensors / Actuators in a location, Cameras or Audio devices in a location, Number of rules that govern the behaviour of a system, the number of Remote Monitoring stations through which the system can be interfaced or the geographical spread. The standard data protocols for machine to machine / Internet of Things connectivity like MQTT, Web socket, Node etc are also adhered to.
A typical example is shown below – a complex entity to manage seemingly dissimilar systems in a factory.
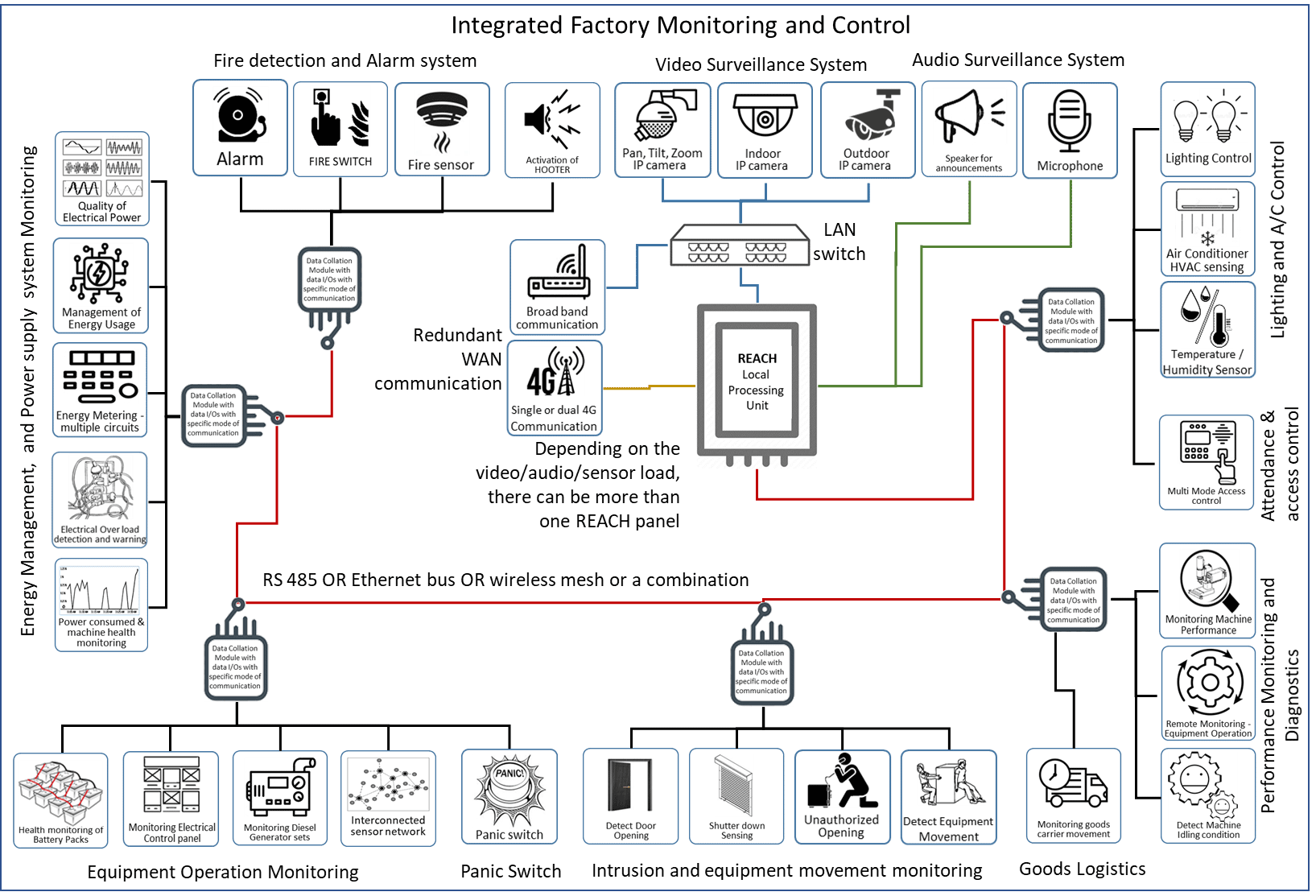
Centralised management system (CMS) is essential in case the system spreads across multiple locations.
The CMS is basically used for the following purposes
- Centralise the controls of all the EDGE systems
- Have a central repository of the data from each EDGE system
- Manage information and control to the Remote Monitoring system managed by Human Operators
- Manage information and control to the Mobile Monitoring managed by authorised Human Operators
- Execute all the rules for the EDGE system which does not have local processing
- Execute all the rules which pertains to data from multiple EDGE locations
- Manage Video wall and bandwidth aware video communication
- Manage Email and SMS communication
- Facilitate external voice communication through mobile network
- Manage the software and hardware assets in all locations
- Run Trouble ticketing and escalation system
- Consolidate the reports from all the EDGE system
- Distribute the reports automatically to the authorised
- Intimate the alerts to the operator of authorised and escalate as designed
- Provide two-way video and audio communication between the RMS or Mobile user and the respective EDGE location
- Access and analyse the logs in the respective EDGE systems
- Facilitate remote operation of equipment at the respective EDGE location
- Conduct software updating automatically across the entire network as required
- Facilitate automatic commissioning of the entire EDGE system, modules, and sub modules in the respective EDGE system
- Maintain the communication with all the EDGE locations
- Ensure system security and data communication security
- Configure access to the system and implement multifactor authentication
- And many more functionalities ….
[/expand]
Remote Monitoring Station (RMS), Mobile access and Interfaces
RMS are the installations from where the entire network is monitored and managed. It provides the human interface for the operators to view the predefined monitoring screens as per authorisations. It is also the location where the system admin can get access to the CMS. The various other activities that are carried out through RMS are commissioning the system, assist in adding devices at a location, Trouble ticketing, report generation, user authorisation management etc.
[expand]
Typical CMS and RMS architecture is shown below
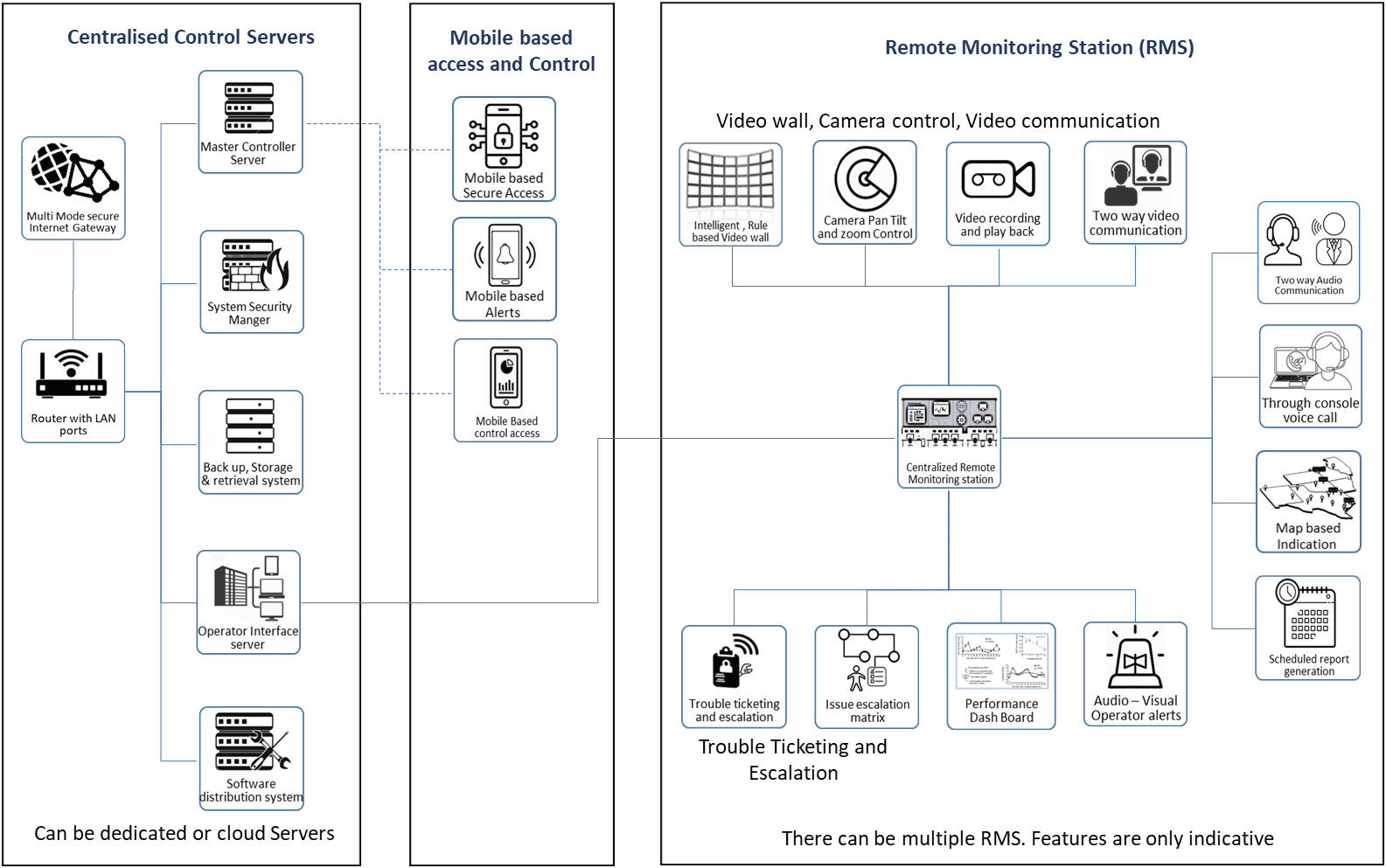
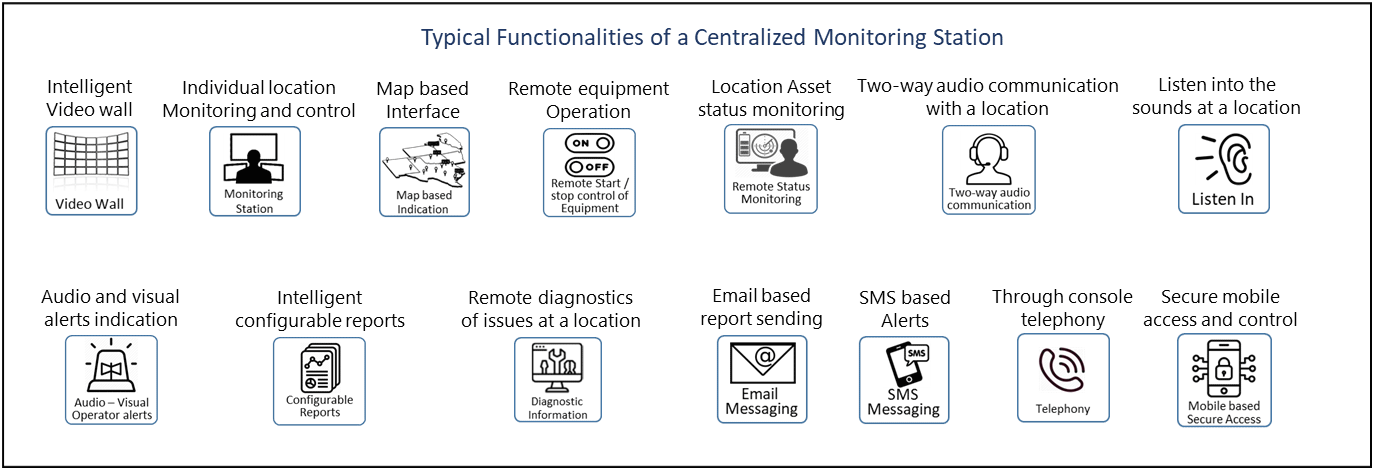
The following are the typical interfaces generated for the operator for different applications. Each application shall have its own interfaces as per the need of the customer.
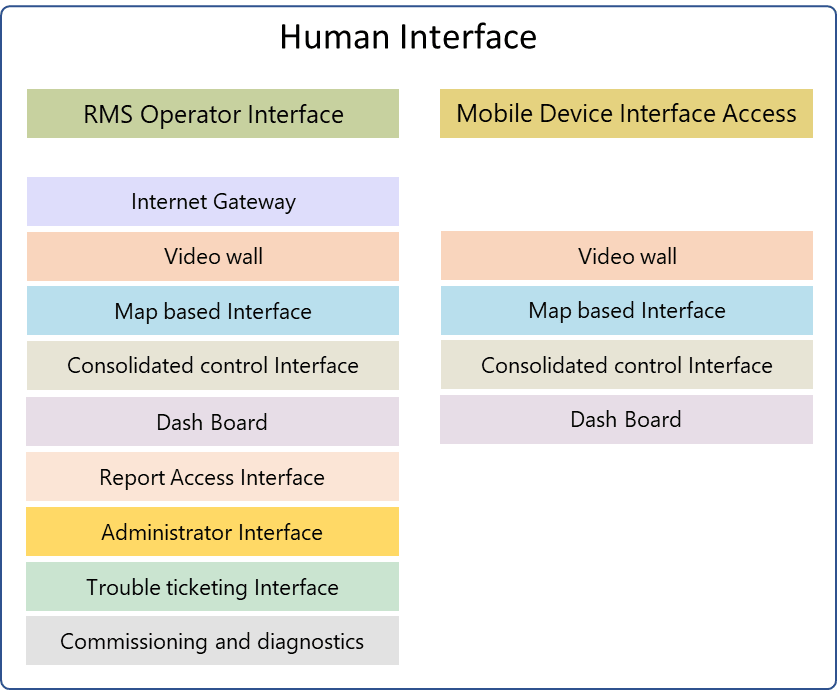
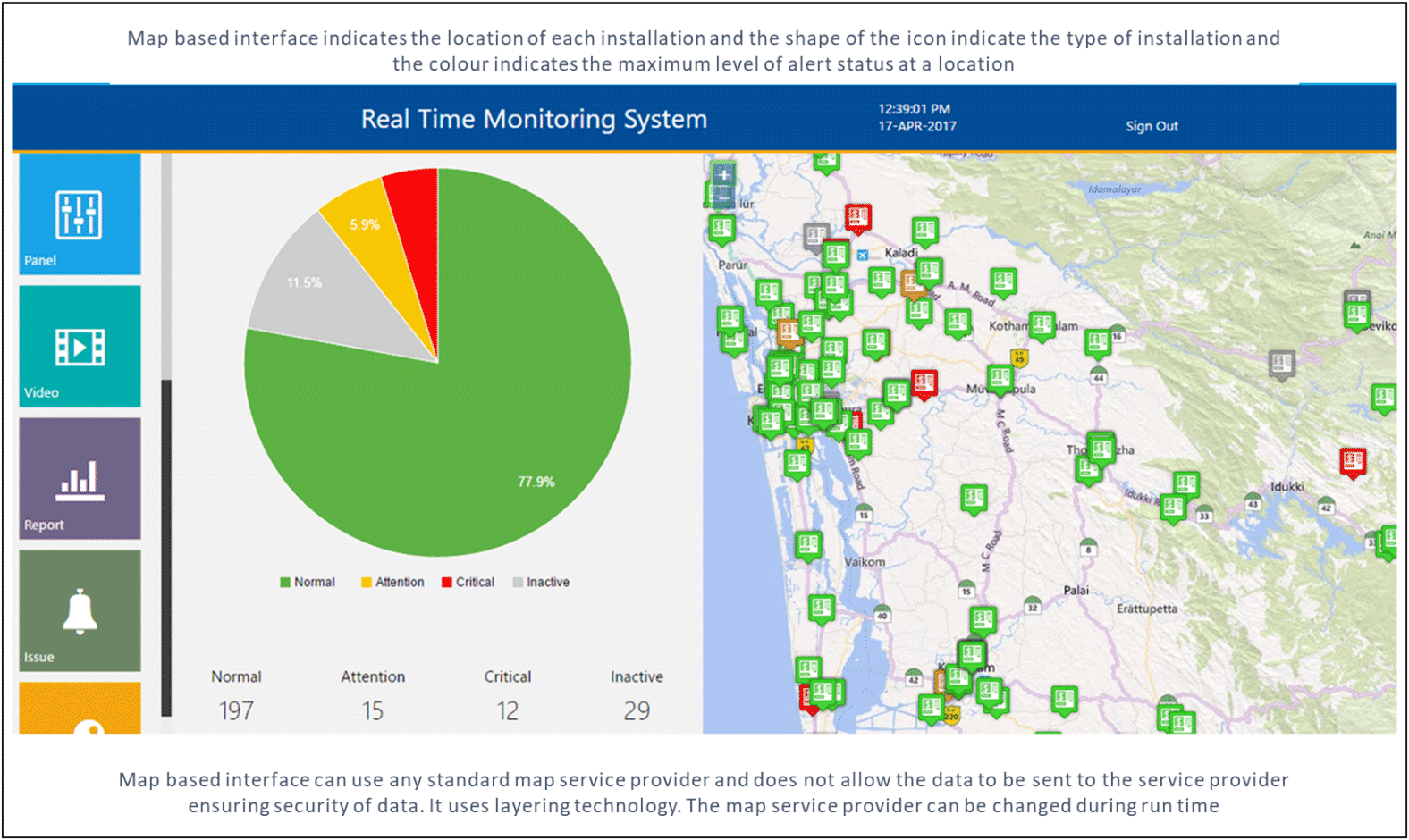
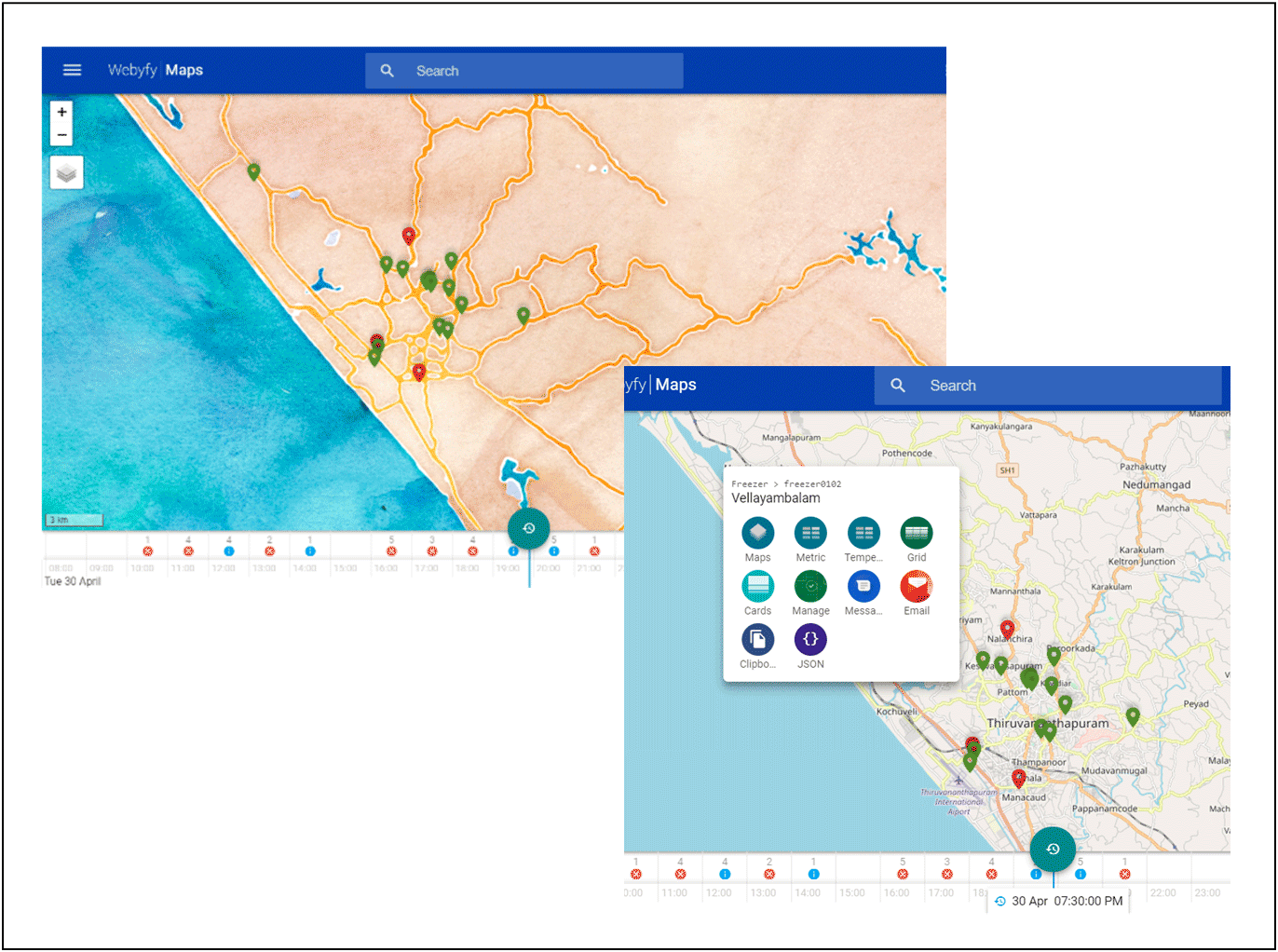
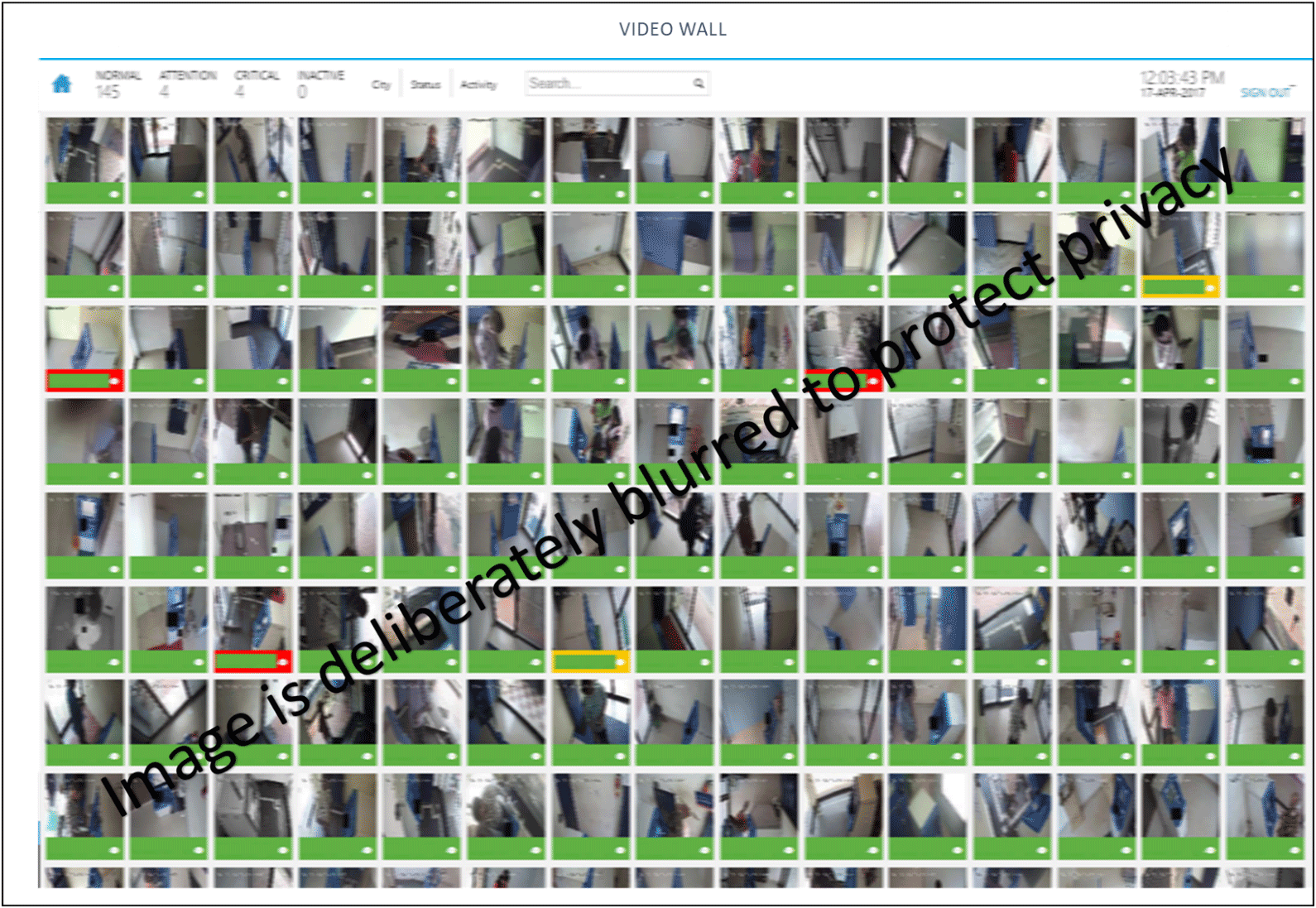
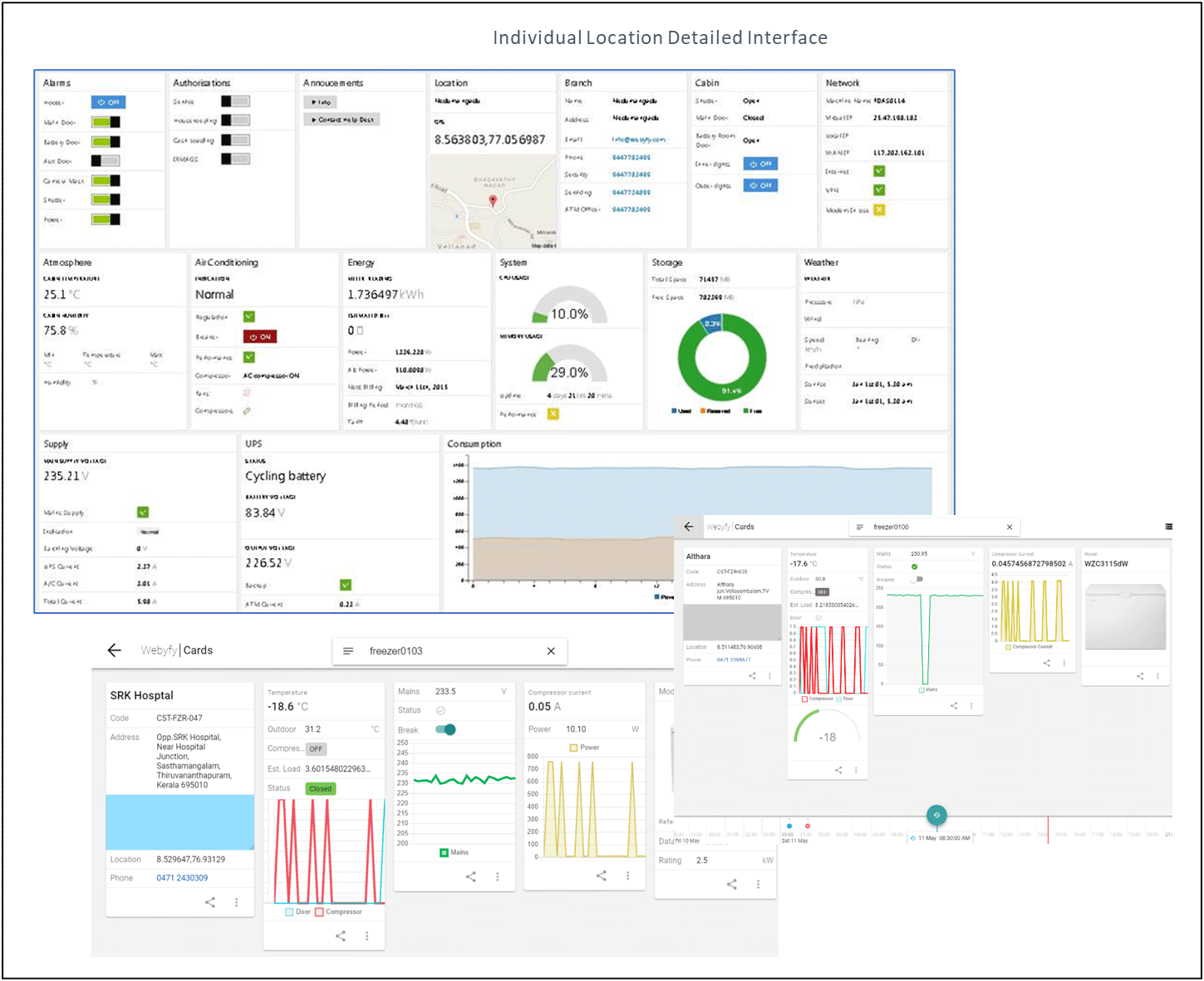
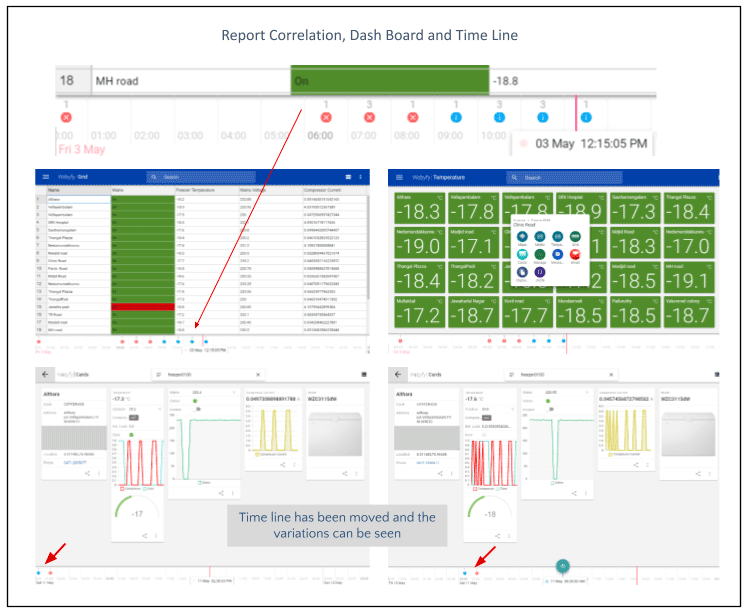
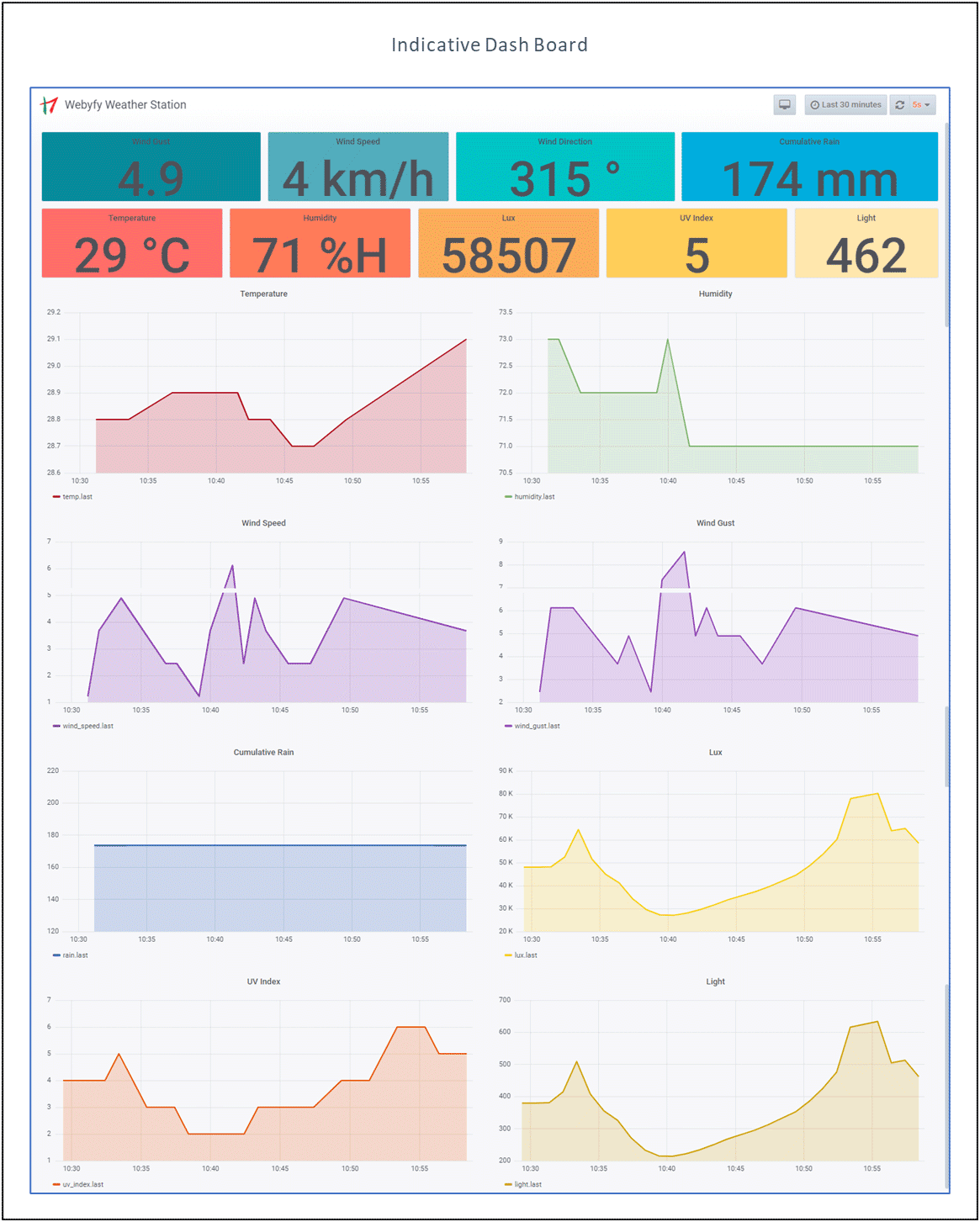
[/expand]
Rule engine and Rule execution
REACH has a very robust Rule engine. These Rules depend on values from multiple sensors or are derived from inputs from video, audio etc. The rules can also be altered according to manual interventions from authorized operators.
[expand]
Rules are defined and executed for a specific location or in every location or a group of locations or for a specific operation in a specific location. Rules can drive operation or set off warnings or initiate communication or send a set of data to a specific location or alter display or interface etc.
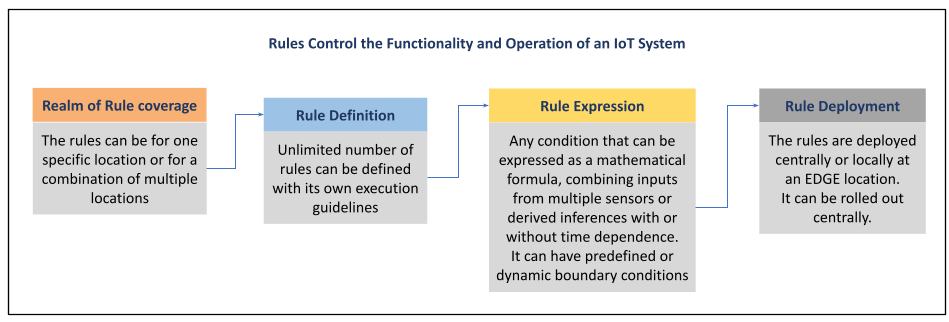
| Examples of Rule Operation Monitoring and Alerts | |
|---|---|
| Boundary conditions while the working of a DG set like excessive jacket water temperature, low oil pressure, high oil temperature, excessive running even if power is restored, non-automatic starting, Power output, voltage stability shall render an effective operation | |
| The health of a UPS and its battery bank can be continuously monitored through rules based on main power availability, UPS output voltage, Battery terminal voltage at different conditions like charging, discharging and floating, charging current etc. | |
| The secure operation of an electrical panel board can be monitored with appropriate rules based on temperature of the bus bars at multiple points, vibration levels, power output to different circuits etc | |
| The water pump can be operated based on rules formulated by the time of day, schedule, peak power tariff duration, water level in the recipient tank, water level in the sump, etc. Appropriate alerts can be generated | |
| The effectiveness of Solar panel and its maintenance point can be arrived at from the DC voltage and current it generates at the time of day. Vandalism can also be detected using a vibration sensor employing 3D accelerometer. | |
| Rules to detect Intrusion shall need the inputs from PIR or other types sensors, IP cameras which detect presence, personnel authentication modules to ascertain the person, Door or shutter opening sensors and the working and holiday schedule. |
[/expand]
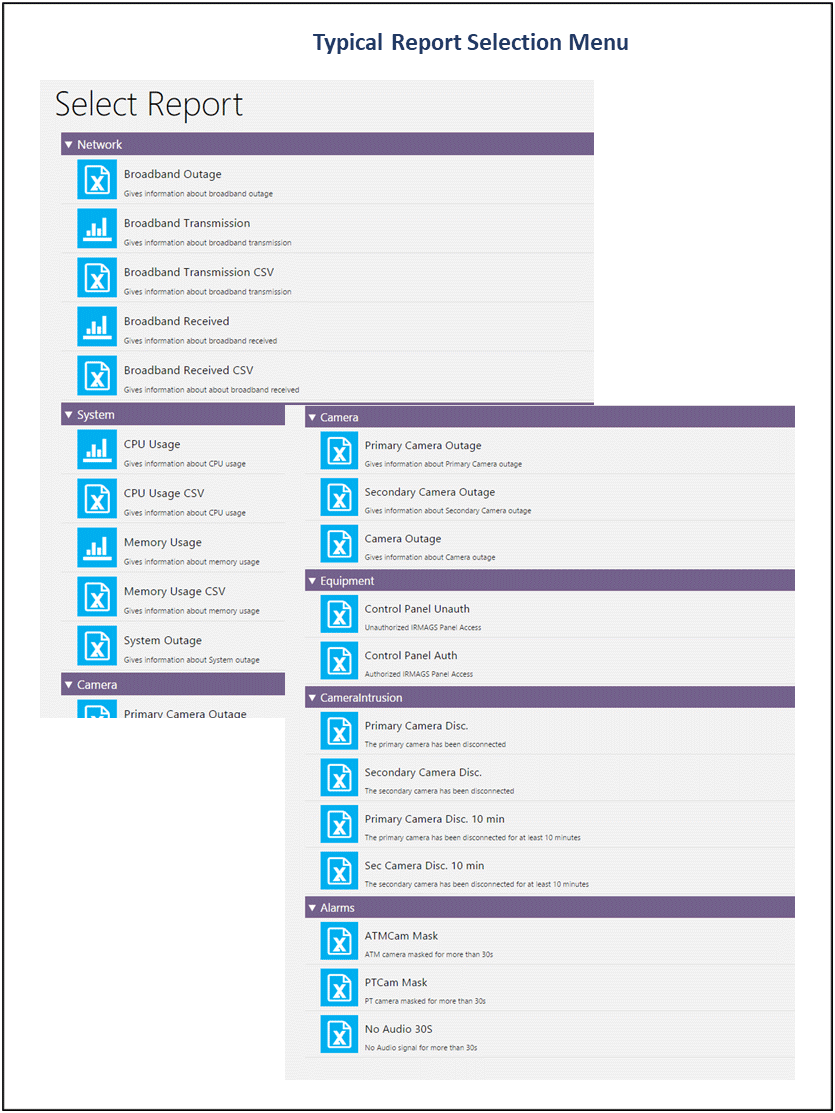
Reports and DSS
REACH has an independent report generation module. Any kind of report can be generated as all the data and the operations are logged. It has been observed that the report requirements are quite varied and hence the reports are created ONLY at the end the system installation.
[expand]
Report generation uses a rule driven engine which consolidates data from multiple sources and generates reports for a period. The report engine also has a dispatch system which sends the reports to authorized persons through email of other means as per schedule. The reports are automatically generated and is in CSV formats for easy downstream manipulation. Decision Support System is two-fold – real time system is enabled through an extensive alert and warming system which can use complex rules. The operator gets real time messages and he either acts on it or escalates as per the matrix. The other mode of DSS is enabled through appropriate reports sent to authorised users as per schedule or predefined rules.
[/expand]
GPS based System Tracking
REACH has the hardware and software modules which can carry out GPS Tracking. The standard GPS module is used for this purpose. Various country specific GPS tracking can be implemented by using appropriate modules. There are various modules based on size and feature stipulations.
[expand]
REACH systems can work on 12 V Dc supply and can have integrated solar panels. This enables all the previously mentioned system to be installed on a moving system like an earth mover, JCB, heavy transportation vehicles or other light vehicles.
This can also be use for tracking vehicles and people. The features are configurable and the rule engine manages the operational process of the system.
REACH has built in modules for the following functionalities
| REACH can track a vehicle or an asset fitted with GPS module in real time. This Can be displayed on a map-based interface. It can use any map service provider. | |
| Geo fencing can be implemented for restricting the movement within a predefined geographical area. Appropriate warnings will be issued as per rules. | |
| No restriction on the number of concurrent assets tracked. | |
| Geo data is stored and the route of the tracked asset can be replayed. This data can also be used for further processing. | |
| Rules can be defined to generate alerts as per the tracked data. | |
| REACH supports voice communication with GPS device installed in a tracked asset. Auto pick up feature enables the listening to the sounds at the tracked asset. This voice also can be recorded. | |
| In addition to GPS tracking of the vehicle, Video surveillance system can be installed on a vehicle and monitored from a Remote Monitoring Station. | |
| The GPS module is considerably small in size and can be attached to an asset. The movement and any deviation from its route or movement from a predefined position can be tracked. It can also detect if an asset is stationary beyond a predefined period at a location | |
| Other features | In addition to the above, REACH has built in functions for low battery alarm, disconnection of power supply, monitor battery voltage, detect engine running, sudden acceleration, detect shock or free fall, asset being stationary, facilitate action like cutting of fuel supply or battery supply, monitor fuel level, provide an SOS button on the asset etc |
[/expand]
Features and Functionalities Built into / Developed using REACH
Functionalities are either built into REACH for easy implementation or can be derived using it. The following list is NOT exhaustive and there are scores more….
[expand]
| Multiple types and makes of cameras | |
| REACH supports multiple makes and types of IP cameras in a single installation. ONVIF supported DVRs and NVRs can also be integrated. | |
| IP camera alerts and video analytics | |
| The system captures IP camera-based alerts and process video & use them as inputs to the rules or display in the interface or to raise alerts | |
| Play Video and Audio Advertisements | |
| REACH provides the facility to play audio or video advertisements in a specific location. The schedule and language of the advertisement can be configured. | |
| Video Wall, Alerts, and Remote Camera Operation | |
| The video wall shows all the video feeds on a screen. Remotely control pan/tilt/zoom camera. Record & retrieve videos and get camera-based alerts. | |
| Two-way audio communication | |
| Two-way audio communication between an authorized user at a specific location, listen-in, automatic rule-based or manual announcement | |
| Support multiple type of sensors | |
| REACH has the capability to integrate any type of industry-standard sensors or actuators. Custom made sensors can also be integrated. | |
| Voltage and Current sensors | |
| The performance of equipment can be understood by the current it takes. The voltage and current variations can be used for protection. | |
| UPS and Battery Monitoring | |
| The status of UPS in indicated by measuring input and output voltages. Battery health is shown by terminal voltage, charging current and its duration. | |
| Energy Management | |
| Energy meter modules measure electrical energy consumption. It measures active and reactive power, power factor, frequency voltage, and current. | |
| Illumination Control | |
| Automatic switching of lights as per rules like time of day/schedule, illumination level, intrusion, etc. There is a provision for manual override. | |
| Simple Movement sensing | |
| The simple sensors which detect motion and movement like PIR sensor, Reed switch, can be used to detect a variety of movements | |
| Movement sensing | |
| Complex sensors like 3D accelerometer are used for sensing rotation, vibration, degree of tilt. Specific sensors for each of these can also be used. | |
| Panic switch and alarms at a location | |
| Visual alarm, auditable alarm, and announcements in case of an emergency situation like pressing the panic button, or based on Operator action | |
| Fire and smoke detection and warning | |
| REACH supports multiple fire & smoke sensors and fire switches, installed with tamper-proof detection. Automatically raise alerts and intimate concerned. | |
| Irrigation control | |
| REACH can be very effectively used for irrigation control. Intelligence can be built-in using soil moisture, weather condition, water availability, etc. | |
| Control of Air-conditioning | |
| Air-conditioning systems can be monitored. Current consumption, room temperature, and humidity. The system can be operated intelligently. | |
| Monitoring of Machines | |
| Performance of machines is deducted by measuring the temperature at multiple points, vibration levels, fuel consumption, energy consumption pattern, etc. | |
| Authenticated Access Control at a location | |
| Multiple modes of access control like Numeric key, fingerprint scanner, RFID, face recognition, eye iris scanner etc. Access code can be altered dynamically | |
| Operator and Authorized User Interface | |
| A specific site interface provides the user the status, facilitates remote operations and dashboards and reports. Map-based interface indicates all locations. | |
| Operator Actions | |
| The authorized user can switch on and off equipment, monitor the status of the operation, control the functioning of installations at a remote EDGE location. | |
| Alerts and Alarms | |
| Based on multiple predefined rules, alerts are generated for a specific location and displayed. Audio and visual alarms can indicate alerts. | |
| Access and Control using Mobile Device | |
| Access EDGE location using a mobile or any internet-connected device. Get alerts, operate devices, view videos and have two-way audio communication. | |
| Configurable Reports | |
| REACH has a configurable report generation engine that creates multitudes of reports and sends them via email or link via SMS as per schedule. | |
| Location detection using GPS and associated functions | |
| REACH has GPS modules which detects location and motion of an asset and calculates several functions like heading , speed, acceleration, geo fencing… | |
| Support multiple internode communication protocols | |
| In a local (EDGE) system sensors & actuators may be spread over a large area. Multiple modes of local communication to EDGE processor are provided. | |
| Multiple, redundant of Internet connectivity | |
| REACH communicates securely using multiple modes of communication. Switches automatically to secondary mode as primary becomes unavailable. | |
| Secure communication | |
| The entire system is within a VPN cloud. The software router can enforce blacklisting and white listing of IP addresses and provide dynamic encryption. | |
| Multi Factor Authentication | |
| REACH has built-in multi factor authentication system configured to the needs of the application. OTP by email/SMS, finger print, USB key etc. | |
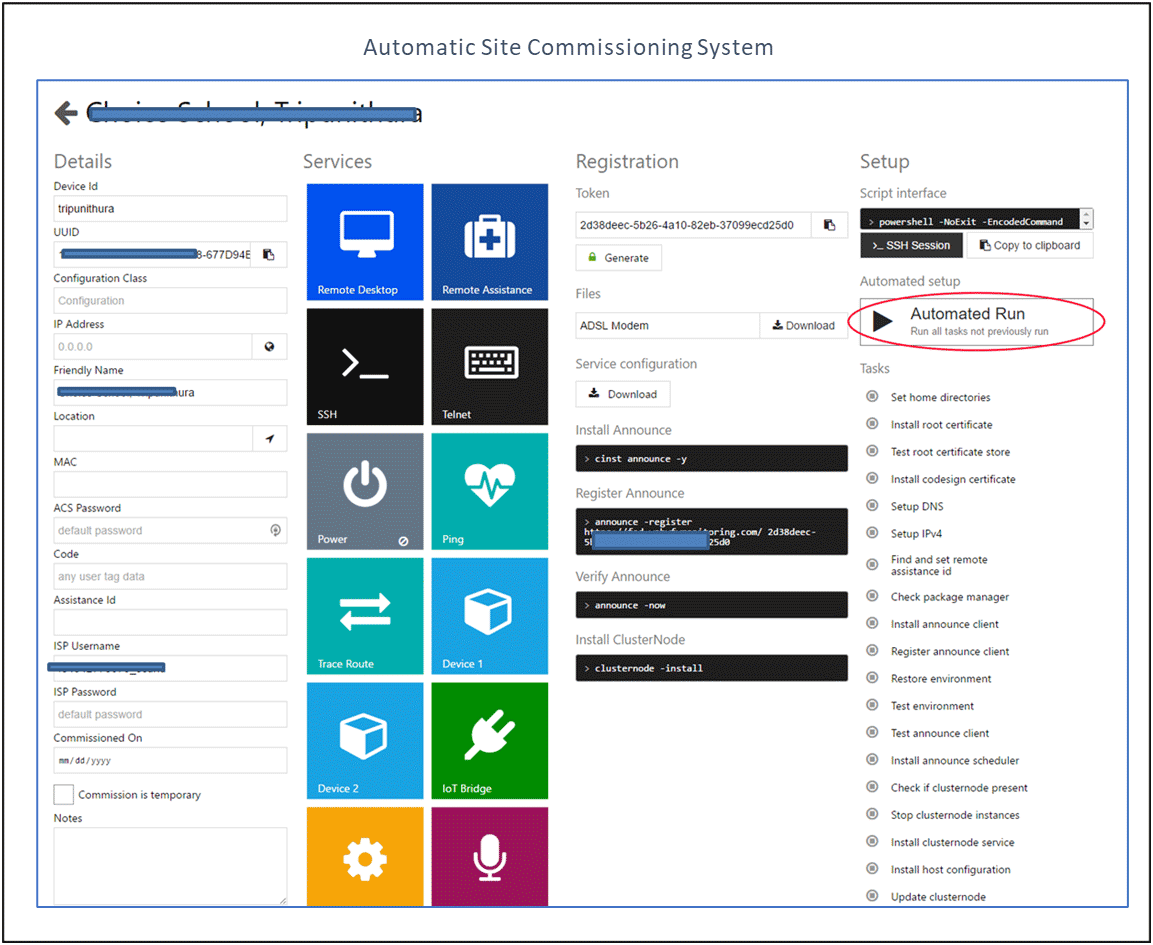
| Automatic, Intelligent Commissioning System | |
| Automatic and intelligent commissioning system requires little technical expertise. The same system can also be used for diagnostic purposes. | |
| Trouble Ticketing and Escalation | |
| REACH has a separate module for trouble ticketing which records issues. They are assigned and escalated as per definition. |
[/expand]
REACH - its uniqueness
The uniqueness of REACH is its capability to create solution almost instantly through its configuration and rule engine without any additional programming or hardware development effort. It is designed to accept any industry standard device in case the appropriate hardware is not available in Webyfy’s module basket.
[expand]
It is IIoT and AIoT ready without any modifications.
- Very high scalability for simultaneous management of thousands of systems
- Completely independent, location-based monitoring and control system which can continue its efficient operation even if connectivity to Central Monitoring Station (CMS) is lost
- The embedded software works on RTOS which facilitates appropriate priority settings and processes execution.
- Location based and Distributed processing eliminating need for centralized processing infrastructure
- Distributed data storage eliminating the need for expensive centralized data centers or NOCs
- Highly optimized and compressed data communication minimizing bandwidth requirement
- Executes intelligent rule-based operations with multiple inputs from varied sources.
- Real time data acquisition and processing.
- Intelligence to escalate to a human intimation / assistance mode when rules are exceeded.
- Automatic switch over when primary means of communication fails and revert when restores. Can have as many fail-safe communication levels.
- Secure Map based Interface with facility to switch map service providers in real time.
- Data not represented with APIs of map service provider to safe guard data being sent to the server of the service provider
- Automatic switch over of assets to another RMS when communication is lost to the designated one.
- Can change sensors or output devices or configurations without affecting the system
- Highly fault tolerant system
- With GPS module, it has location specific Rule configuration for movable Assets.
- Centralized software updating
- Two-Way Audio / Video communication
- Rule Based Video wall with unlimited videos.
- Automatic trouble ticketing system with multiple modes of Escalation
- Automatic IVR, SMS and Email integration at local asset and central control room levels
- Through system voice calling facility of operator And many more
Why one should adopt REACH over competition?
The key features that bring in significant befits to customers are:
- Once the process is defined the solution can be configured almost instantly. So, the cycle time from idea to application is very little.
- Designed to enable rapid prototyping and quick alterations to arrive at the final requirement
- Highly scalable with no limits to the number of devices it can handle.
- Webyfy has designed and developed most of the modules and hence it is backward compatible.
- The system is designed to have modifications while in operation – One can add on modules or remove them or change behavior and interface by changing the rules
- The interface is uniform across the devices to minimize the learning time
- Very cost effective compared any of the competition
- Assured and designed in quality to operate without failures
- Fault isolation and very high fault tolerance so that the system will continue to function in the most unlikely event of failure of individual module.
- Built in diagnostics to identify deviations and rectify them
- Supports any industry standard device to be integrated and hence not married to specific make or model.
- Supports multiple makes of devices to work seamlessly in a single system.
[/expand]